The importance of IT and Cyber Security is constantly increasing due to the digitalisation of all areas of life, work and business. Due to the use of the Internet in more and more processes and tasks in administration and companies, but also in the private sector, we are highly dependent on functioning information technology and secure information infrastructures. Ensuring security in the World Wide Web and the protection of critical information infrastructures have become existential issues of the 21st century and require a high level of commitment from all those involved. Networks are converging worldwide, so that cyber attacks in other countries can also have an impact on IT security in Germany.
Security in the Internet of Things
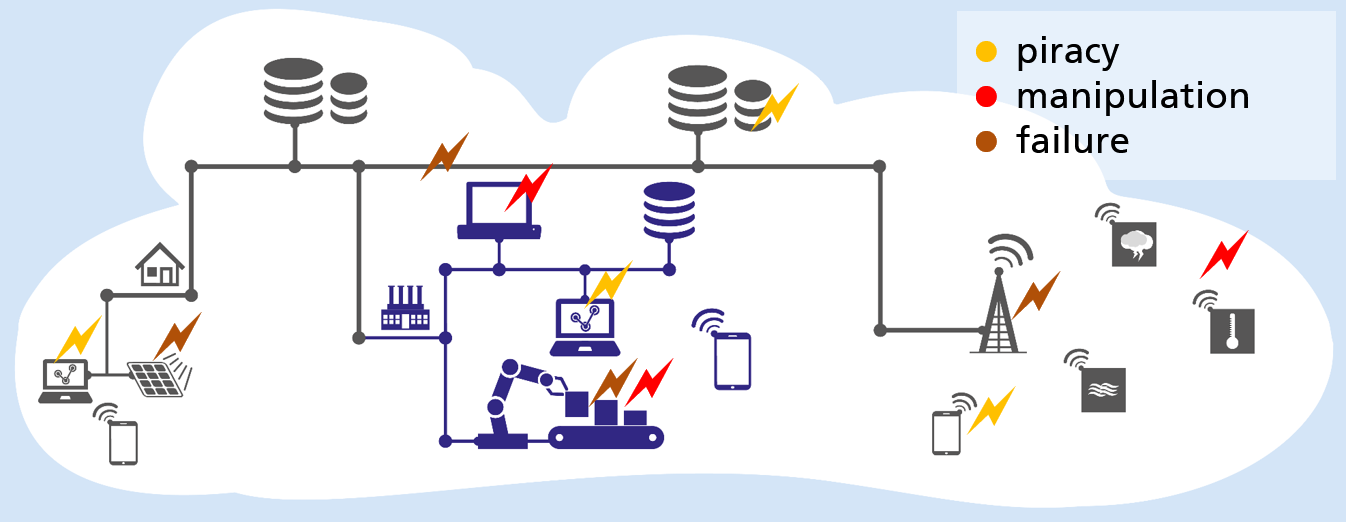
The Internet of Things merges the real world with the digital world. As a result, the previous reliable protective wall between these worlds is disappearing more and more, so that cyber attacks can have real effects in everyday or professional life. Due to the limited resources available in cyberphysical systems on the Internet of Things or in sensor networks, conventional security mechanisms and techniques such as firewalls, intrusion detection systems or anti-virus software cannot be used.
Protective measures for wireless devices
Wireless devices are potentially exposed to cyber and hacker attacks due to their functions, especially their connection to computer networks or the Internet. The conditions imposed by the limited resources usually have a direct impact on the IT security of these systems. Tried and tested and partially standardized procedures and procedures often cannot be applied and the guarantee of the protection goals must be adapted to the special circumstances.
Networking challenges
The challenges of increasing networking are the drastic increase in possible points of attack. By 2020, an estimated 50 billion end devices will be integrated into our everyday lives on the Internet of Things. Security depends on the weakest system component, often the sensor node. Systems are becoming more complex and distributed. The sovereignty over a system is distributed among a large number of independent actors. This creates a major trust problem.
In contrast to consumer technologies, which have a lifetime of only 2 years (mobile phones), Industrial IoT uses systems that are often in use for several decades. In general, the challenge is to enable consistent data confidentiality, integrity and authenticity in data communication on the Internet of Things.